30+ threat model data flow diagram
You should regularly run a data. What kind of threat model needs building.

Graphing The Utility Grid On Aws Aws For Industries
The model can be understood simply by its name which stands for Goal Reality Obstacles Options and Way Forward.

. The model is meant for setting goals and problem solving. List the kind of data that will be processed or stored. From observing others one forms an idea of how new behaviors are performed and on later occasions this coded information serves as a guide for action Bandura.
Most human behavior is learned observationally through modeling. The daunting threat of antimicrobial resistance is of particular importance in the category of antibiotic resistance in bacteria. These interconnections are made up of telecommunication network technologies based on physically wired optical and wireless radio-frequency.
The water cycle also known as the hydrologic cycle or the hydrological cycle is a biogeochemical cycle that describes the continuous movement of water on above and below the surface of the EarthThe mass of water on Earth remains fairly constant over time but the partitioning of the water into the major reservoirs of ice fresh water saline water salt water and atmospheric. Even if you are not asked to bring a 30-60-90 day plan it might not be a bad idea to bring along one to improve your chances of scoring a job. Furthermore the database backups are kept in geo-replicated storage to ensure resilience from regional catastrophe.
Moving from left to right along one health impact row the three middle columns show how climate drivers affect an individuals or a communitys exposure to a health threat and the resulting change in health outcome. The answer requires studying data flow transitions architecture diagrams and data classifications so you get a virtual model of the network youre trying to protect. A computer network is a set of computers sharing resources located on or provided by network nodesThe computers use common communication protocols over digital interconnections to communicate with each other.
This is our main data entry on plastics with a particular focus on its pollution of the environment. It is not a security review a full threat-model a vulnerability assessment or an audit. Temperature and Pressure - Online calculator figures and tables showing specific heat C P and C V of gasous and liquid ammonia at temperatures ranging from -73 to 425C -100 to 800F at pressure ranging from 1 to 100 bara 145 - 1450 psia - SI and Imperial Units.
The tree is a conceptual diagram showing how an asset or target could be attacked consisting of a root node with leaves and. User flows are diagrams that help UX and product teams map out the logical path a user should take when interacting with a system. The examples listed in the first column are those described in each underlying chapters exposure pathway diagram.
8 Antibiotic resistance compromises a human. Threat actors then deploy the ransomware to the datasets and systems of highest importance or value leaving the organization compromised. As you define your environment its important to ask all organizations and departments if they receive cardholder information and then document how their answers may change card data flows.
A CHD flow diagram is a graphical representation of how card data moves through an organization see adjacent example. We have also produced an FAQs on Plastics page which attempts to answer additional common questions on the topic. Treasury Takes Actions in Zimbabwe.
Based on the well-established concept that multi-organ failure is a proximal cause of death in sepsis 10 we sought to evaluate whether the LPS-primed neutrophils prevent lethality by preserving. You can also restore these. As a visual tool the user flow shows the relationship between a website or apps functionality potential actions a user could take and the outcome of what the user decides to do.
An ammonia phase diagram are included. Firepower Device Manager lets you configure the basic features of the software that are most commonly used for small or mid-size networks. These types of activities may however follow an RRA if deemed appropriate or necessary.
A typical Rapid Risk AnalysisAssessment RRA takes about 30 minutes. In addition the Long-Term Retention LTR feature allows you to hold onto your backup files for a much longer period specifically for up to 10 years and restore data from these backups at any point within that period. The first synthetic plastic Bakelite was produced in 1907 marking the beginning of the global.
A slide-deck summary of global plastics is available here. People learn through observing others behavior attitudes and outcomes of those behaviors 1. Treasury Announces Five Additional Capital Projects Fund Awards to Increase Access to Affordable High-Speed Internet.
View all Featured Stories. In addition to this tactic threat actors actively monitor the communications and planned recovery actions of an organization to undermine response efforts and further infiltrate networks and connected devices. 3 According to the CDC more than two million people in the United States become ill with antibiotic-resistant diseases every year resulting in a minimum of 23000 deaths.
Ammonia - Specific Heat vs. This guide explains how to configure Firepower Threat Defense using the Firepower Device Manager web-based configuration interface included on Firepower Threat Defense devices. Daily Treasury Par Yield Curve Rates.
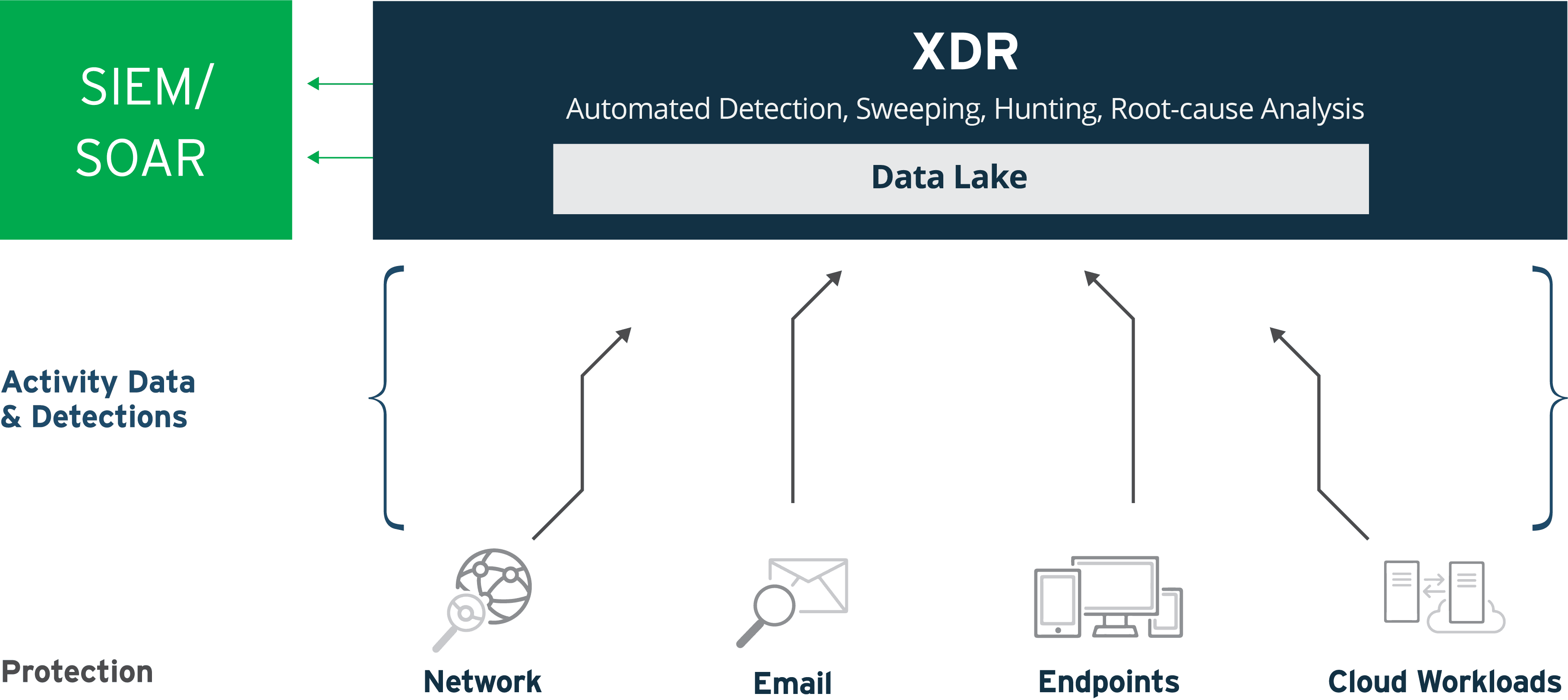
What Is Xdr

A Threshold Based Real Time Analysis In Early Detection Of Endpoint Anomalies Using Siem Expertise Sciencedirect
How To Design A User Flow Diagram For Your Website
![]()
Threatmodeler About The Evolution Of Threat Modeling
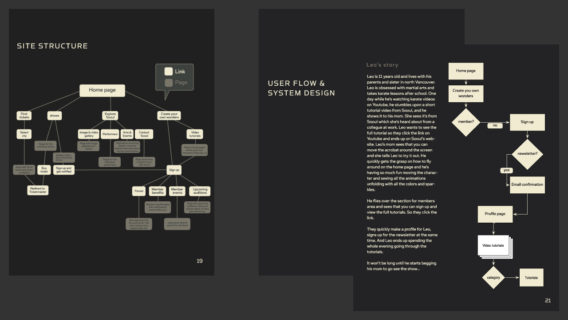
How To Design A User Flow Diagram For Your Website
What Is The Purpose Of Developing Dfds Quora
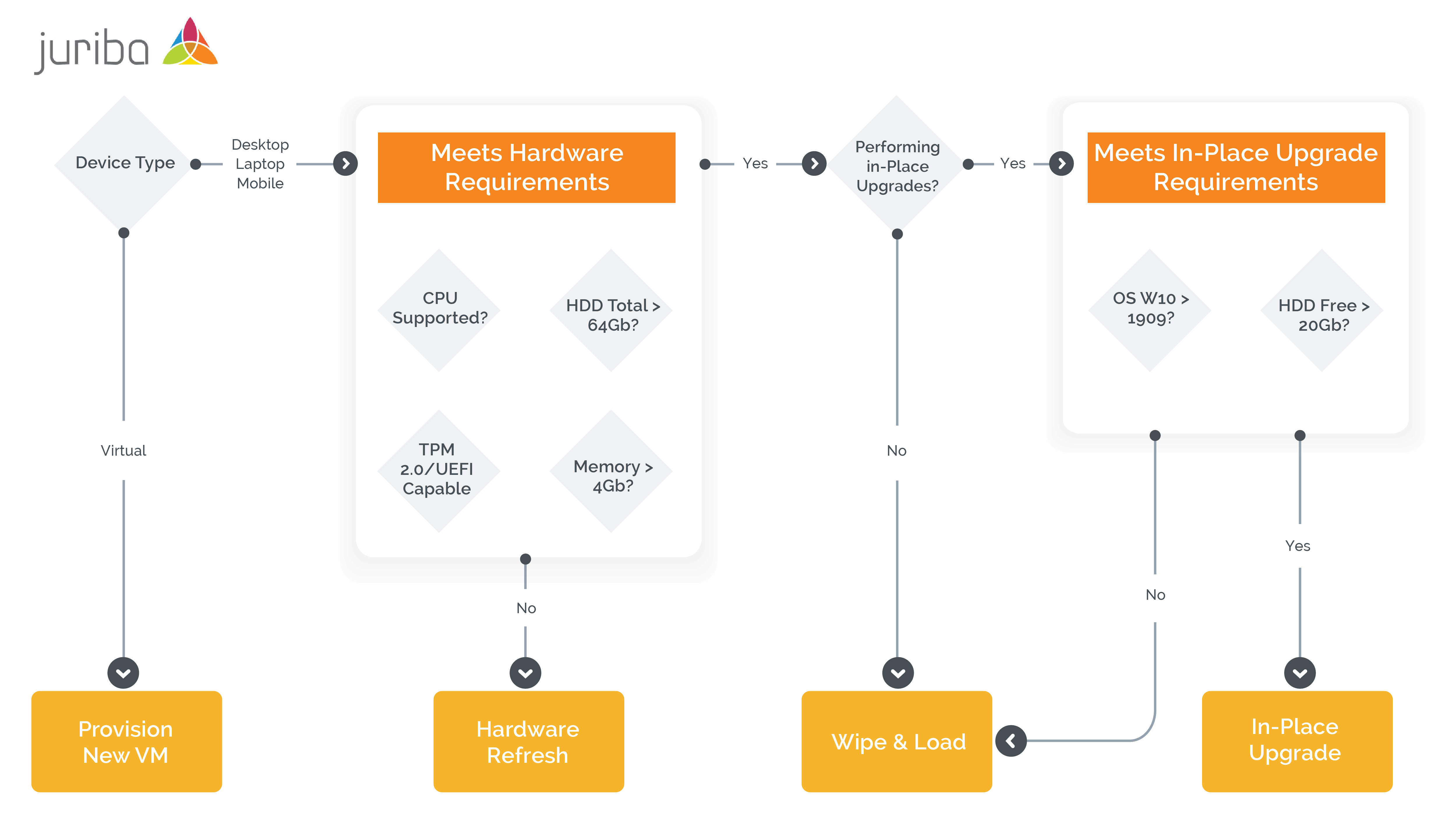
In Place Wipe Load Or Hardware Refresh How Windows 11 Hardware Requirements Will Determine Your Migration Strategy
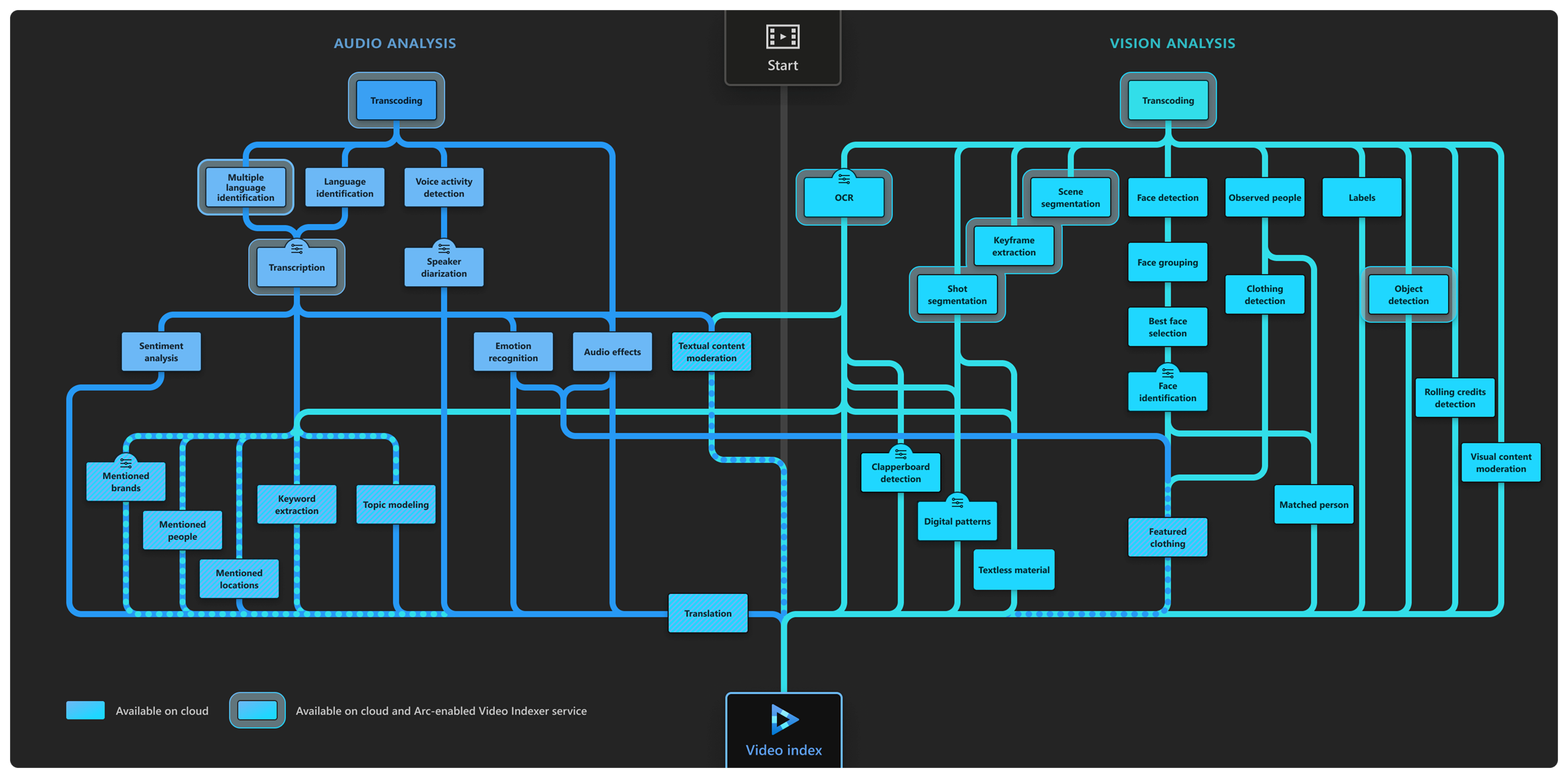
What Is Azure Video Indexer Azure Video Indexer Microsoft Docs

Code Quality Tools Tame Software Complexities Circuit Cellar
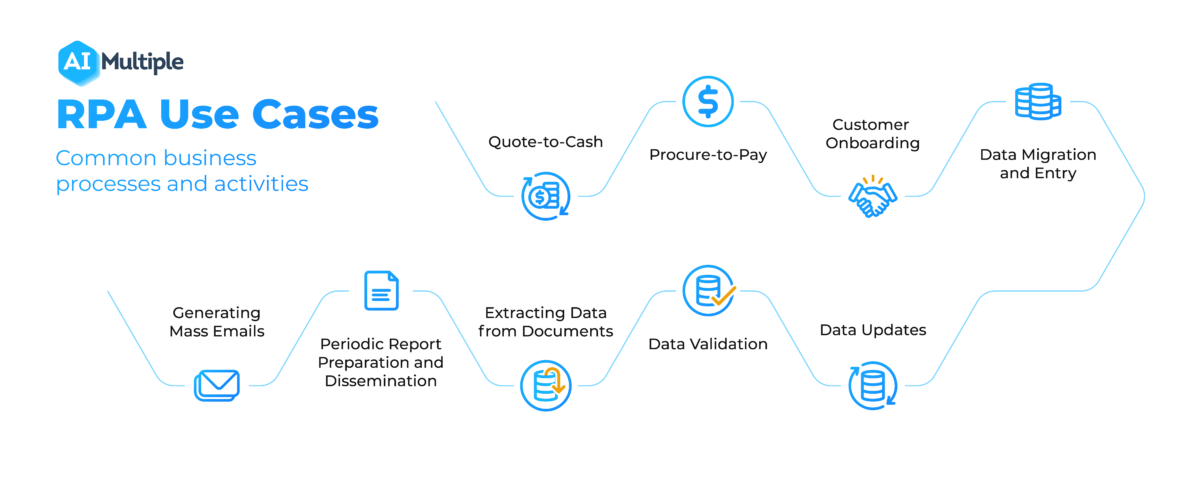
100 Ai Use Cases Applications In 2022 In Depth Guide
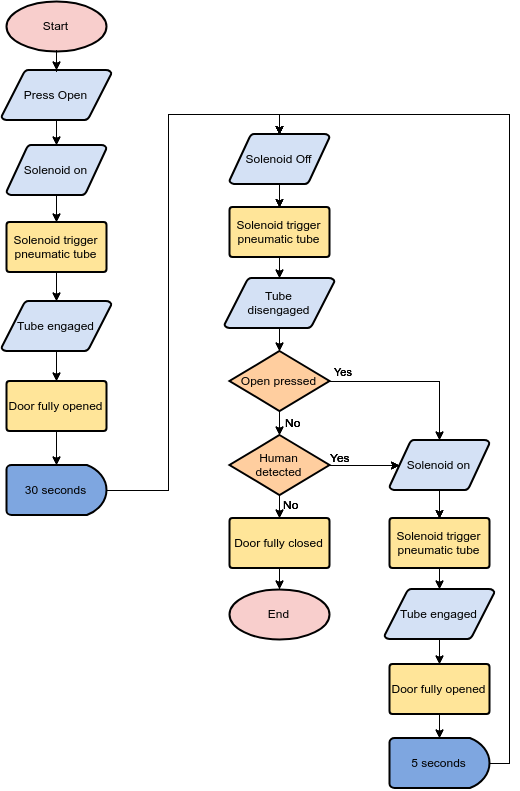
A Comprehensive Guide To Flowchart With 50 Examples Cybermediana
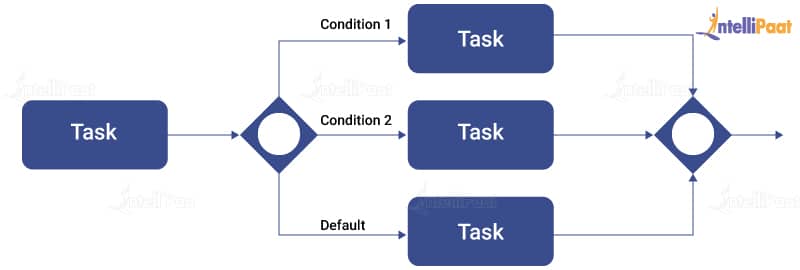
Top 35 Business Analyst Interview Questions And Answers 2022
T2isd79la4he3m
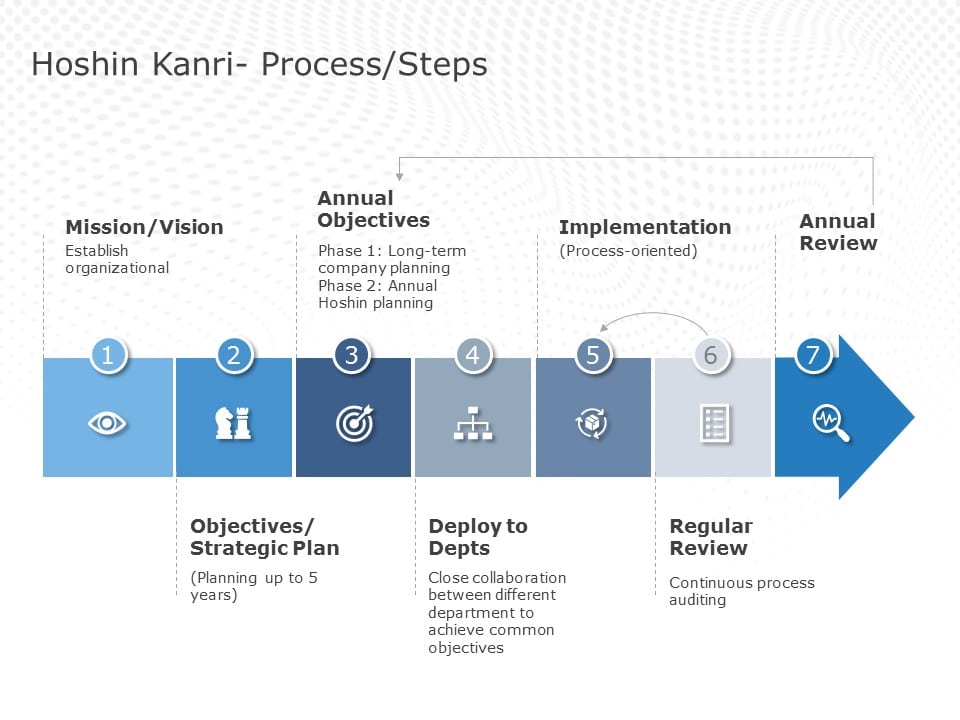
1567 Editable Free Flow Chart Templates Slides For Powerpoint Presentations Slideuplift

Graphing The Utility Grid On Aws Aws For Industries
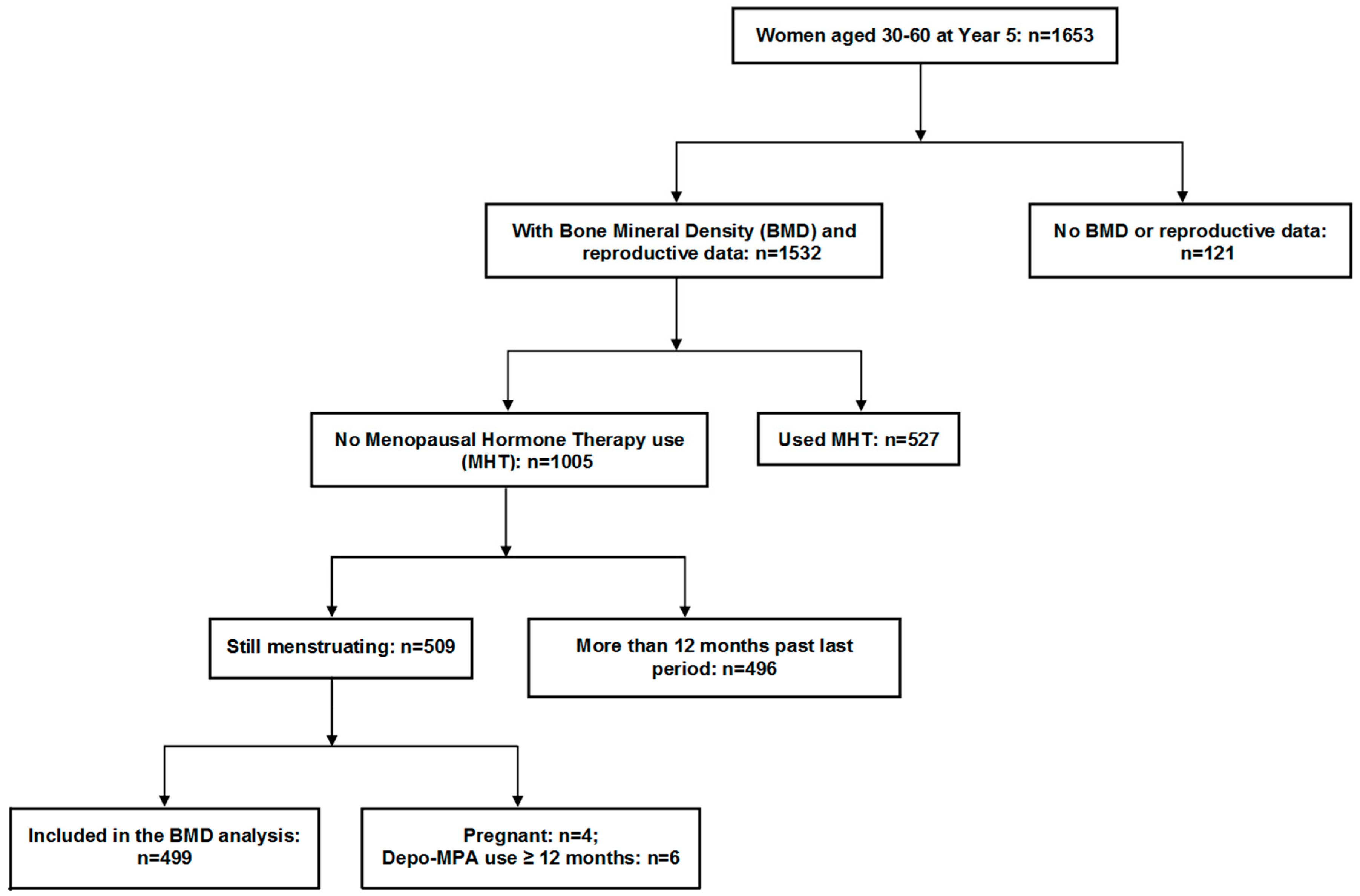
Ijerph Free Full Text Adult Premenopausal Bone Health Related To Reproductive Characteristics Population Based Data From The Canadian Multicentre Osteoporosis Study Camos Html

Navin Ramankutty Nramankutty Twitter